Managed Security
The 5 Pillars of Secure IT for Emerging Companies
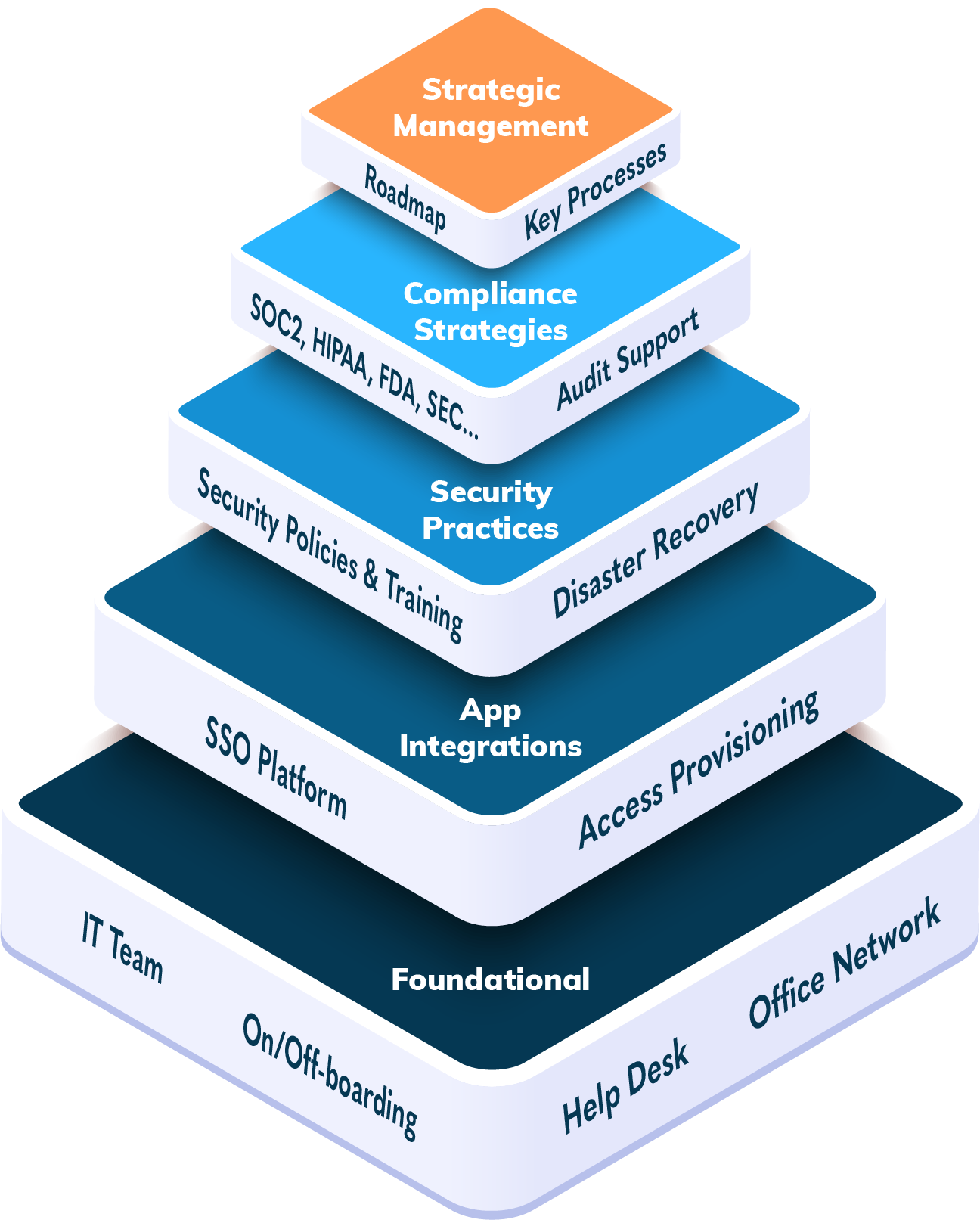
When it comes to IT security, emerging venture-funded companies are not like small businesses or large enterprises. They need a secure foundation and an ongoing program to manage security without a lot of expense or resources.
With over 20 years’ experience providing IT and security for emerging life science and technology companies, KalioTek has developed a practical, affordable program that covers all the important bases. It evolves as your company grows and the threat environment changes. Security awareness and protection never end, but you can have peace of mind that industry best practices for companies like yours are being employed.
The 5 pillars of a security program are:
User – Audited Access Rights
- User credentials are the weakest link. To make sure they are not stolen, train your people in safe cyber hygiene, including multi-factor authentication. Limit each user to the data and system access necessary for their roles. Audit access to all systems regularly as people come and go.
Threat Detection and Response
- Secure Endpoints Devices – Each device with access to company data is verified to be encrypted and protected by a centralized endpoint security system. With the right endpoint management tools you can push updates and security patches to remote devices that are not connected to the network, and lock or wipe devices when needed.
- Log collection and analysis – Real-time analysis and escalation, often called SIEM (Security Information and Event Management), backed by a 24×365 SOC (Security Operations Center).
Network – Network Access Control
- The network is segmented for security and protected by redundancy and security devices. It is monitored for failure and attacks. Logs are saved and securely stored. Access, including wireless and VPNs, requires authorization and is restricted based on role.
Data – Confidentiality, Availability and Integrity
- Wherever data is stored, it is encrypted and only accessible by authorized users. It is available to them when they need it, and we can ensure it has not been altered by unauthorized sources. Secure backups and a Disaster Recovery plan are in place and tested regularly.
Governance – Regulatory Compliance, Insurance
- Necessary policies have been specified, communicated and are being followed in the organization. Controls are in place to provide evidence when audited. Appropriate cybersecurity insurance is in place.
Contact us to learn more about the details and how these can be implemented in your company.